How to Protect Against WordPress Zero-Day Attacks

When it comes to cyber security, what you don’t know can hurt you. This is exactly the case with zero-day vulnerabilities and zero-day attacks. The repercussions of not taking your security seriously can be devastating to you and your business.
Fortunately, the best weapon you have in your arsenal against malicious hackers and security threats is educating yourself on security risks, security best practices, and potential zero-day vulnerabilities that can leave your WordPress sites open to attack.
That preparation is the focus of this article. Read on, and we’ll show you six ways to keep your WordPress website safe from zero-day attacks.
What is a Zero-Day Attack?
A zero-day vulnerability happens when malicious actors or hackers discover a security flaw in a piece of software and exploit it to gain unauthorized access to your WordPress site. It’s important to note that the security hole must be unknown to the developer for it to be a “zero-day” vulnerability.
A zero-day attack or zero-day vulnerability gets its name from the fact that once the vulnerability disclosure is known or made public, you have exactly zero days to make the site secure and protect against the vulnerability by releasing a security patch that solves the security issue in question.
This often involves working round the clock and can be quite an unpleasant experience. But, if you fail to release a patch in time and the hackers discover the vulnerability before you, the consequences can be dire.
Let’s take a look at some common ways that hackers use to attack vulnerable systems:
Fuzzing: Fuzzing is a type of brute force attack that hackers use to access your system. Fuzzing involves using software to enter all kinds of random, nonsensical values into the various input boxes of your website. Almost every website has input boxes for typing in things, including the search bar, the text box on your login page, etc. When the code for the site has holes in it, hackers can detect vulnerabilities by looking for crashes when they spam the input boxes with nonsensical data.
Pretexting: Pretexting is when a hacker uses a false pretext to gain private details that give them access to your account. In such situations, hackers will pretend to be someone else (usually a technical support executive or someone from your bank) and ask you for your account details under the pretext of solving some issue.
Phishing: When someone convinces you to give away confidential details, open malicious files, or click a corrupted link by impersonating someone you know, it’s called a phishing attack. Like pretexting, phishing is a form of social engineering. Once a hacker has gained access to your account, they can use it to look for vulnerabilities from inside the system.
How a Zero-Day Attack Can Harm Your WordPress Site
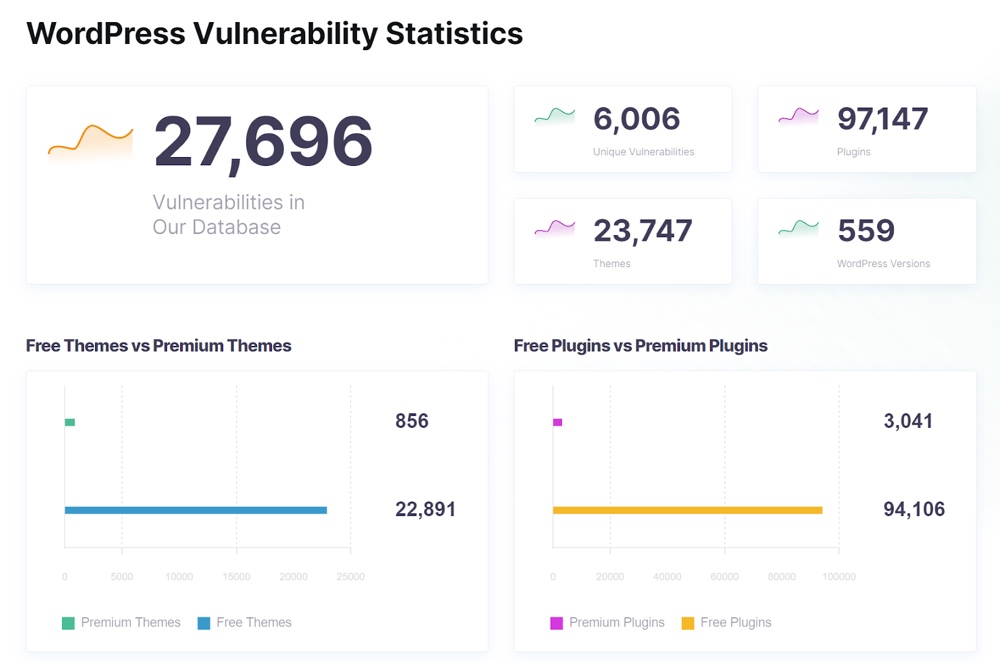
Source: WpScan
When a group of hackers discovers a flaw in your software or WordPress website, they can write very specific malicious code to take advantage of the security vulnerabilities. Unfortunately, these vulnerabilities are often not obvious to the layperson. They then package this code into malicious software or malware. This is referred to as a zero-day exploit.
The final goal is to use the zero-day vulnerability to access the system and use it in ways it was never intended to be used. This can include:
- Corrupting site files through malware
- Stealing important data from both customers and administrators
- Spamming your customers, subscribers, or readers
- Installing software that steals important information and leaking it
Site owners need to prevent zero-day vulnerability attacks because the repercussions from not doing so can be devastating to their organization or business. Fortunately, you can follow best practices to deter such attacks from happening most of the time.
Inside the Zero-Day Exploit Market

Zero-day vulnerabilities are rare, and like all rare commodities, there exist markets for them. The code for zero-day vulnerabilities can be bought and sold, and these codes garner the interest of hackers, government authorities, other brands, and military intelligence agencies. And, while several ethical hackers may look for zero-day vulnerabilities in software or WordPress websites and voluntarily alert the developers to software vulnerabilities, these people are still looking for monetary gain.
In general, there are three categories that the zero-day exploit marketplace can be divided into. These are:
- The Black Market. This comprises the underground marketplace where exploitation codes are traded.
- The Grey Market. When hackers sell zero-day exploit codes to the government, military, or intelligence agencies in order to exploit them for surveillance purposes.
- The White Market. This refers to all the researchers and ethical hackers who find and share zero-day vulnerabilities with the software vendors to help fix security issues. This is usually the most ethical group.
How to Protect Your WordPress Site Against a Zero-Day Attack
Now, if you’re the owner of any WordPress sites, you’re probably wondering how you can protect your site from being taken advantage of by malicious actors and serious zero-day threats.
There are several steps you can take as a website owner (even if you’re not very tech-savvy) to beef up your site security. Let’s take a look at some of them:
1. Keep WordPress Core and Plugins Up-to-Date
Keeping your WordPress core and plugins up to date is one of the surest ways to prevent a zero-day vulnerability. When security researchers or hackers discover such a flaw, developers rush to release a patch. Ensuring that you have the latest version of the software often means that you can patch the vulnerability and stay protected.
This is one of the reasons you might want to turn on auto-updates (especially for WordPress core). Auto-updates will now automatically download and install the latest version of its core software and include all security updates not just major releases. It’s also recommended you set auto-update on for WordPress plugins and themes.
Additionally, if you’ve created your own WordPress plugin, you might want to double-check to make sure it’s secure regularly.
2. Disable Old Themes or Plugins
Though WordPress core isn’t immune to zero-day attacks, themes and plugins are typically the most susceptible.
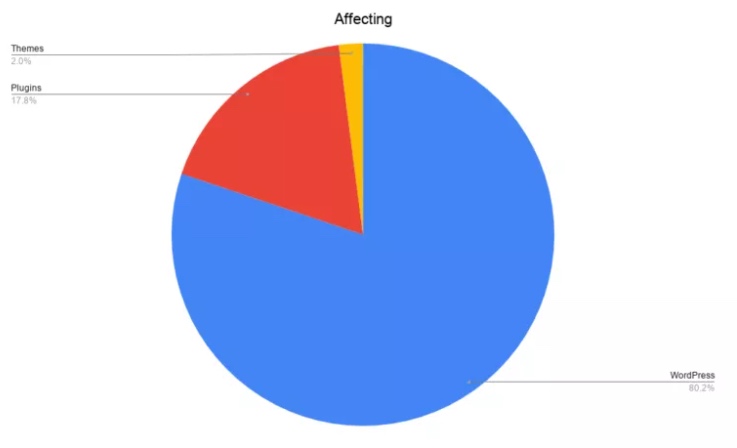
According to recent statistics, approximately 17% of all WordPress vulnerabilities are from vulnerable plugins, and about 3% are from WordPress theme vulnerabilities (however, these numbers may be inflated because multiple versions of WordPress have to be considered).
Either way, it’s thankfully relatively easy to protect against attacks on themes and plugins.
Instead of waiting for a patch, you can just delete the themes or plugins until a patch is released. Disabling them alone doesn’t always protect you from security risks as you can still face security risks to sensitive files from deactivated plugins and themes.
Of course, this depends on whether or not your business can afford to operate temporarily without the said plugin. On occasion, you might be forced to operate with the vulnerable plugin temporarily (for example, if you’re using something crucial – like a language switcher plugin or an accessibility plugin).
3. Use a Plugin to Spot Suspicious Activity
There are several WordPress security plugins available to help you look for and identify suspicious activity. One excellent option is a WordPress activity log that can track detailed changes in any activity and maintain your website security.
Using a VPN is also a great way to encrypt all private data to avoid being taken advantage of and having your data used by actors with bad intentions. A good VPN will also block malicious phishing sites and keep you safe.
You can also use active plugins, such as WordFence Security, to check your site’s core files, themes, and plugins for malware. It also keeps an eye out for underlying zero-day vulnerabilities by looking out for code injections and malicious redirects.
However, WordFence Security needs to be placed in learning mode to collect data for at least a week to prevent false positives. This ensures that it won’t accidentally flag legitimate actions as suspicious.
4. Get a Firewall

Firewalls are digital walls that function as barriers between your system and the outside world. In order for a hacker to take advantage of your system, they must first breach the firewall. Thus, firewalls add an extra layer of protection to your WordPress site.
There are several types of firewalls to choose from, such as a personal firewall to protect your operating system, packet filtering, stateful, web application firewall, Next-Generation (NGFW) firewalls, etc.
If a vulnerability is discovered, you can still block the attack if you have a firewall included among your security services. Specifically, you can block some of the most common attacks (such as Structured Query Language (SQL) injections and Cross-Site Scripting (XSS) attacks) with the help of a decent firewall.
5. Adopt Cyber Safe Behaviors
Making sure you follow best practices and adopt a policy of only cyber-safe behaviors is a great way to avoid unnecessarily putting yourself at risk. The security industry usually has best practices you should be following. Let’s take a look at some of them:
- If you want to add a safe QR code generator, a home screen callout, or build a Windows live tile, make sure to double-check to ensure it’s cyber safe. These are often vulnerable.
- Avoid clicking on unknown links and going to questionable pages.
- Don’t download files of data from unknown publishers, no matter how tempting it is (this data is unlikely to help you anyway, as you can’t verify its quality).
- Always ensure that you select optimum WordPress security settings that follow the recommendations from your software vendors.
- When adding elements like a “contact us” form to your website, use a reputable WordPress form maker like WPForms and consider how you design your forms carefully to protect against fuzzing.
Additionally, if you’re using a managed WordPress hosting company that offers a secure hosting provider, make sure you read up on the hosting company and its security standards.
6. Watch for WordPress-Related Disclosures
Finally, it’s a good idea always to keep yourself updated on the latest security news and security software. You can always read about recently hacked websites and the exploited flaws.
Additionally, join a disclosure mailing list and watch for disclosures from plugins/themes/software vendors. Or follow a WordPress related news outlet like WPTavern. It’s also a good idea to keep track of bugs that someone could potentially exploit.
Keep in mind that to keep most users safe, a vendor will often have to delay announcing the existence of vulnerabilities until they have created a patch. While this can help minimize the number of attacks, it also means that you will be using insecure software, which leaves you vulnerable. Stay vigilant, and report anything suspicious to the vendor immediately.
Zero-Day Exploit Proofing Your WordPress Site
While it may not always be possible to eliminate the chances of a zero-day vulnerability entirely, there is certainly a lot you can do instead of waiting around.
What makes zero-day vulnerability attacks difficult to deal with is the fact that since these vulnerabilities haven’t always been discovered by the vendors yet, there are not always solutions immediately available. But, by following everything mentioned in this guide, you should have more than enough knowledge to manage your WordPress site until a patch is released successfully.
And even in the absence of a vulnerability being discovered, the guidelines outlined in this article should arm you with the best possible practices to keep your website safe.