DDoS Attacks & How to Keep Your WordPress Site Safe

Generally, business owners are always thinking of strategies to optimize their WordPress site for greater traffic influx and higher rankings that can help them get greater visibility. All their efforts will go to vain if the site ends up being hacked, though, which isn’t only a costly affair but can also compromise the reputation of the brand.
WordPress offers powerful features and a secure codebase, making it one of the most popular website builders globally. But this doesn’t make it immune from various forms of malicious cyberattacks, such as DDoS attacks that are increasingly becoming rampant in today’s time.
In this guide, we’ll talk about DDoS attacks in greater detail, along with steps that you can take to manage your website security like a total pro.
What is a DDoS Attack?
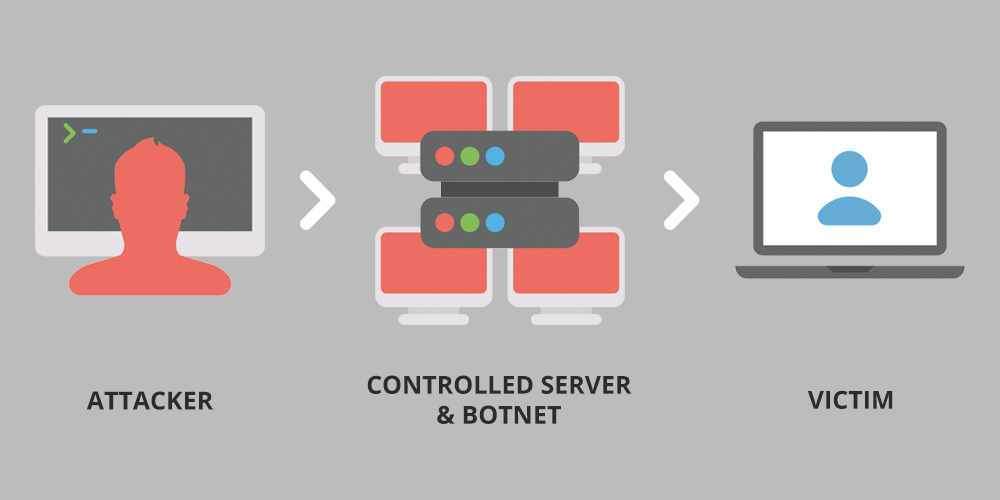
A DDoS attack is a short form for Distributed Denial of Service attack. It’s a type of cyber attack that utilizes compromised computers and devices for sending and requesting data from a WordPress hosting server, allowing a malicious user to gain control over your site. Most popular WordPress hosts include measures to mitigate the risk of DDoS attacks, including encrypted connections, continuous monitoring, and plugin vulnerability mitigation.
Think of DDoS attacks as a more evolved form of DoS (Denial of Service attacks). Unlike the latter, DDoS attackers manipulate multiple compromised machines or servers to enhance their spread across different regions.
The compromised machines then create a network (also known as a botnet), with every affected machine acting as a bot and launching attacks on the targeted server or system. This also allows them to remain undetected for some time, permitting them to cause maximum damage before the real owner is successful in blocking them.
What Happens During a DDoS Attack?
We’ve already discussed how compromised machines create a botnet in a DDoS attack. Before we delve into the technical aspect of these attacks, we would like to clarify that a bot is an automated program that executes specific tasks online at a speed that is much faster than what humans ever could. This is exactly what the hackers take advantage of.
In a DDoS attack, your server resources are depleted, while the website load time is increased. So when it hits any website, it can cause performance issues or completely crash the server by overwhelming the server’s resources like memory, CPU, and sometimes, even the entire network.
The primary point of origination of these attacks and from a hacker-controlled botnet of vulnerable IoT devices. Since the Internet of Things (IoT) is a rapidly growing internet segment, it makes it more prone to common IoT security threats, especially DDoS. The most common devices being household appliances, smart TVs, security cameras, home lighting systems, and even refrigerators!
What are the Different Types of DDoS Attacks?
Interestingly, DDoS isn’t a single form of attack; there are different varieties with a separate style of functioning that result in several subcategories for classification. Read on as we discuss the most common ones in greater detail below:
Volumetric DDoS Attacks
Generally straightforward, volumetric DDoS attacks involve flooding a target with a request to overload bandwidth capacity without directly targeting WordPress. Instead, the main aim of these attacks is to target the underlying operating system, along with the webserver. Still, volumetric DDoS attacks are relevant to WordPress websites.
If the hijackers are successful, your WordPress site won’t be able to serve pages to genuine visitors throughout the course of the attack. The most common types of these attacks include NTP amplification and UDP floods.
Application Layer DDoS Attacks
Aptly titled, application-layer DDoS attacks focus on layer seven, which is the application layer. Or your Apache or NGINX web server, along with your WordPress website. From all the types, this one certainly causes the maximum damage relative to bandwidth spent.
HTTP floods and Slow Post attacks fall under this category.
The WordPress REST API is a prominent example in this case. The attack starts with an HTTP request from one of the host machines, which then uses a relatively trivial amount of resources on the host. However, this might have an opposite effect on the target server, triggering several operations. The server checking credentials, returning a webpage, and reading from the database, etc., being common examples.
Multi-Vector DDoS Attacks
Hackers don’t limit themselves to just a single type of attack and often take a multi-vector approach. As you might expect, when carrying out a multi-vector DDoS attack, the hacker uses multiple techniques for targeting.
Protocol-based DDoS Attacks
These attacks follow the same exhausting forces model as others but are mainly focused on the transport and network layers as opposed to the application or service. Think of attacks like the ping of death and syn floods.
Hackers launch these attacks to deny service by targeting appliances, such as the underlying TCP/IP stack or firewalls running on your server. It enables them to exploit vulnerabilities in how the server’s network stack handles tasks like TCP communication or network packets.
Methods to Keep Your WordPress Site Safe From DDoS Attacks
It’s crucial to understand that a DDoS attack isn’t a WordPress hack in a traditional sense. These attacks cannot steal a website visitor information – plus, the sole purpose of carrying out these attacks is to overload the website resources, which at times is used for extortion or blackmail.
In 2016, the average annual unit customer churn for SaaS companies was 10%, which is a term used to refer to the loss of a customer. But when a potential customer finds it difficult to load the website, the number can become greater. In such situations, the hacker can ask the website owners to pay a ransom to stop a DDoS attack to keep the website running smoothly.
Here’s what you can do to help prevent these attacks.
Employ a Content Delivery Network (CDN)
Services that cache copies of your website on their respective data centers are known as CDNs. Think of them as a middleman between your site’s visitors and yourself.
The idea behind using a CDN is to reduce the strain on your server that can, in turn, help you decrease the overall loading time as they are specifically built for performance optimization. These also act as a firebreak of sorts to DDoS attacks by restricting resultant traffic from overwhelming your website, as well as to detect anomalous attacks and downs in traffic, mitigating it effectively.
Many hosting companies offer a built in CDN, there are tons of CDN plugins (such as Site Accelerator, as part of Jetpack) or you can use a free CDN from a third party. At WPExplorer, we use and recommend Cloudflare – but choose the option that works for you.
Switch to a New (Better) Hosting Provider

Let’s face it: Web hosts are not the same.
If you choose a hosting provider that isn’t well equipped to handle a moderate strain, it will, of course, make your site the perfect victim for a DDoS attack. Luckily, there are several reputable WordPress hosting providers like WP Engine that have excellent protection protocols against traffic floods at the server level.
Use a DDoS Protection Service

Generally, CDNs offer DDoS protection as an incentive, but you can also sign up for a dedicated DDoS protection service as an alternative. And as one would expect, opting for these services isn’t cheap, with a few companies charging around $3000 per month.
Blacklist Suspicious IP addresses

You should definitely monitor IP addresses that display suspicious activities, such as unreasonably high number of visits, repeated login attempts, and IP clusters, which eventually flood your website with traffic. It’s also a viable option if you don’t want to use third-party services or plug-ins.
Set Up a Firewall

Firewalls are software that has preprogrammed rules to protect your computer from unauthorized access. You can configure your firewall to limit the number of users accessing your website during a specific period and filter out bots – or visitors that are likely to be bots.
Doing this can be very beneficial to stop minimize DDoS attacks without compromising user experience, and is much easier now than in the past. Many digital courses in web development security now include lessons on how to set up firewalls and virtual private networks. And most good WordPress security plugins offer a firewall as a part of their feature list.
The Bottom Line: websites – big or small – often fall prey to DDoS attacks. Hackers use these attacks as a form of blackmail against businesses, which is why you should take measures to scan your WordPress site for vulnerabilities and set up WordPress DDoS protection.
Most WordPress users have a lower possibility of suffering from a DDOS attack – but you still could. Keeping this in mind, it’s always smart to consistently apply the best security practices to enhance the safety of your site.