Cross-site Scripting (XSS): What Is It and How to Fix it?

Being one of the most common cybersecurity threats, cross-site scripting (XSS) attacked nearly 75% of large companies back in 2019. Moreover, almost 40% of all cyberattacks were performed to target XSS vulnerabilities.
Cross-site scripting has affected websites run by web giants like eBay, Google, Facebook, and Twitter. But cross-site scripting is not a new cyberthreat. In fact, XSS attacks have been around almost since the dawn of the web itself.
To help you prevent XSS attacks, this guide focuses on everything you need to know about cross-site scripting. After reading this guide, you’ll get a better idea of how cross-site scripting works and how you can secure your WordPress website.
What is Cross-site Scripting (XSS)?
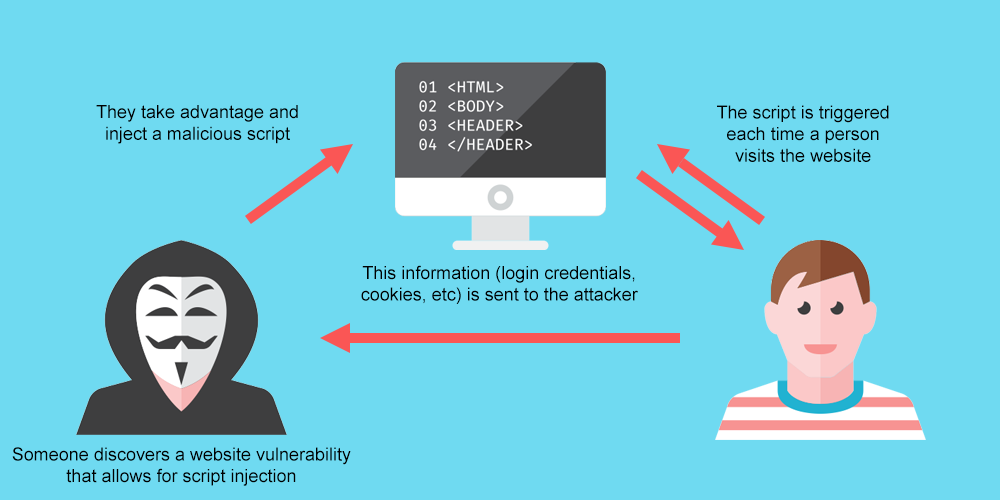
Cross-site scripting (XSS) refers to the type of cyberattacks in which malicious scripts are being injected into otherwise credible and trusted websites.
Cross-site scripting attacks are possible in HTML, Flash, ActiveX, and CSS. However, JavaScript is the most common target of cybercriminals because it’s fundamental to the most browsing experiences.
JavaScript is a programming language that allows you to implement complex features on your website. Most websites on the web that are big and interactive were built with JavaScript. “You can develop on-site interactive features, games, or add extra functionality to better market your products,” per Domantas Gudeliauskas a Marketing Manager for the Zyro project.
JavaScript is so popular among the web community because it lets you do virtually anything on a webpage. And that’s when it becomes problematic. Cybercriminals can use JavaScript to log into the back of your web pages and insert malicious scripts.
How Cross-site Scripting Works?
There are two ways cybercriminals perform XSS attacks on WordPress websites. They can either exploit user input or bypass the same-origin policies. Let’s take a look at both methods to further understand cross-site scripting.
Manipulating User Input
The most common way cybercriminals perform XSS attacks is by exploiting user inputs. Most WordPress websites have user input fields, such as search bars, comment forms, login pages, and contact forms. The input field is typically enabled by JavaScript-powered WordPress plugin or theme active on your website.
The problem is that not all WordPress plugins and themes are 100% secure and many of them do, in fact, have XSS vulnerabilities. What this means for you is that cybercriminals can utilize WordPress vulnerabilities in input fields to run malicious activities.
Ideally, a site search bar (or any other user input field) should only accept plain text, not commands, as an input. However, WordPress does have a user input vulnerability, which allows hackers to enter an executive code into the input field and send it to the database.
Bypassing Same Origin Policies
The same-origin policy restricts one page to retrieve information from other web pages. Under the policy, web browsers allow scripts contained in the first web page to access data in a second web page only if they share the same origin. This helps to ensure that no cross-site requests are made.
The policy states that if you have your Facebook page and online banking opened in the same browser, the two websites can’t share information with each other. Yet, if you have multiple Facebook tabs (that share the same origin) opened, they can exchange script and other data between each other.
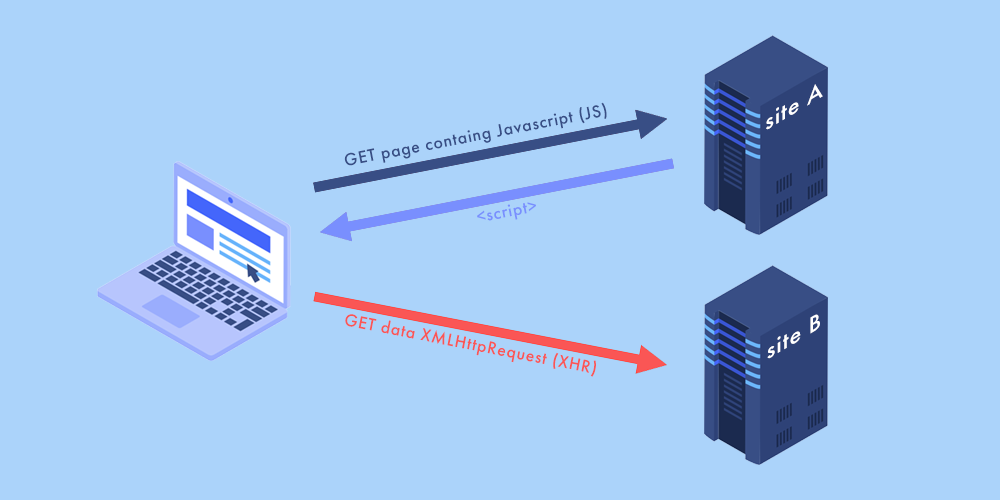
Despite the same-origin policy and other security measures taken to prevent cross-site requests, cybercriminals have found a way around the policy using session cookies. This works because every time when you open a browser, it generates a session cookie to validate you as a website user and help you move from one page to another smoothly.
Session cookies store login credentials (including for your WordPress site), credit card information, shipment details, and other sensitive data. Here’s how it works. Let’s say, you want to login to your online banking account. When you open the website, a session cookie is being generated. If it wasn’t for session cookies, you’d have to log in to your online banking account every time you want to switch pages.
It’s not uncommon for users’ browsers to have vulnerabilities. And if there are any, cybercriminals use code they injected into the user input to steal session cookies. This way, hackers can steal cookies of all websites opened in the user’s browser. Then, these cookies can be used to login to users’ accounts to impersonate them and steal financial data.
Why is Cross-site Scripting Dangerous?
Cross-site scripting is one of the most common high-risk WordPress vulnerabilities. XSS attacks are so common because, unlike other security vulnerabilities, they are very complex to address. Even when you have built-in protection, it’s very easy to make mistakes that enable cross-site scripting. Only one mistake in your web page’s HTML or JavaScript can make your website vulnerable to cross-site scripting attacks.
When attackers find a way to exploit XSS vulnerabilities, they can steal account credentials, financial data, and facilitate phishing scams. They can also spread computer worms or get access to users’ computers remotely. Besides, XSS attacks allow hackers to perform the following:
- Hijack user accounts
- Spread malware
- Control user’s computer remotely
- Scan and exploit intranet applications
XSS attacks are commonly viewed as being less dangerous than SQL injections. However, when combined with social engineering, cross-site scripting allows cybercriminals to pull off advanced and extremely dangerous attacks, including planting trojans, keylogging, phishing, identity theft, and cross-site request forgery.
To battle XSS attacks, large IT companies launch special bug bounty programs. These programs are implemented by many organizations and offer compensation or recognition to the users who report XSS vulnerabilities in scripts. This way, companies are investing in cybersecurity by having other developers identify their bugs. Google even launched a game where you can exercise in dispatching XSS bugs.
Types of XSS Attacks
There are three main types of cross-site scripting attacks: reflected, stored, and DOM-based XSS. To get a better perspective of how XSS works, let’s take a look at each type of XSS vulnerabilities.
Stored cross-site scripting
A stored XSS vulnerability (a.k.a. Persistent or Type I) takes place when user input is stored in a database, comment field, visitor log, or other target servers. And then a victim can retrieve the stored data (that hasn’t been made safe to render in the browser) from the web application. This way, when a hacker performs an attack, the payload is not visible for the browser’s XSS filter, and victims can accidentally trigger the payload if they visit the affected page.
Reflected cross-site scripting
A reflected XSS vulnerability (a.k.a. Non-persistent or Type II) takes place when a web application immediately returns user input in a search result, error message, or any other response. In this case, the user input data is reflected without being stored, thus allowing hackers to inject malicious XSS scripts. Unlike stored XSS, reflected XSS targets the website itself rather than website visitors.
DOM-based XSS
TA DOM-based XSS vulnerability (a.k.a. Type 0) occurs in DOM (Document Object Model) rather than in the part of HTML. The source where the malicious code is read can be a URL or a particular element of the HTML.
How to Prevent Cross-site Scripting Attacks?

Now, as you’ve covered the XSS fundamentals, let’s take a look at the proven ways to prevent XSS attacks.
There are multiple ways you can protect your WordPress website from XSS attacks. If you have advanced technical expertise, you can add code snippets to validate and sanitize user inputs. However, if you aren’t familiar with the technical part of WordPress, it’s better to delegate the work to your tech team or hire a professional who can take these measures for you.
In the meantime, there are two things you can do to prevent cross-site scripting attacks.
Install a security plugin
Installing a security WordPress plugin is the first step towards the ultimate security of your WordPress website. When choosing a security plugin, use this checklist as a reference to ensure the plugin has the functionality required to keep your website safe.
- A plugin regularly scans your website for malware.
- A plugin uses firewalls to block any traffic that seems malicious.
- A plugin is capable of implementing WordPress hardening measures.
- A plugin allows you to manage all WordPress updates.
- A plugin backs up your WordPress website, so in case of attack, you can restore your website.
Install a dedicated plugin
Installing an anti-XSS plugin is another way to prevent cross-site scripting. Anti-XSS plugins work by blocking parameters that are commonly used in cross-site scripting attacks. For example, these plugins can secure user input fields, such as your website’s comment forms, login fields, or search bars.
The bottom line – 39% of all WordPress vulnerabilities are connected with the cross-site scripting issues. Companies lose millions of dollars trying to battle the consequences of cross-site scripting attacks. In order to avoid XSS attacks targeted on your website, it’s important to understand what cross-site scripting is and take preventative measures.
To keep your website safe from cross-site scripting, you should validate and sanitize your input fields. Additionally, you can install security and dedicated anti-XSS plugins that will help you keep your WordPress website secure.